Expediting in Procurement: An Essential Guide
The fundamentals of expediting in procurement, including the scope, importance of, challenges, best practices, future trends, and more!
Latest Posts
RFP, RFQ, RFT, RFO, RFI, or RFEI? An Essential Guide
Request for X? In procurement, the acronym RFX means Request for X, where X is a variable that stands in for different types of bid invitation...Construction Materials Management: An Essential Guide
While most people identify construction material management with purchasing and distributing construction materials, the reality is more complicated....Spend Under Management: An Essential Guide
Taking Control of Your Spending In today's competitive business landscape, managing your expenses effectively is more important than ever. But with a...
Latest Posts By Category
- Procurement
RFP, RFQ, RFT, RFO, RFI, or RFEI? An Essential Guide
Request for X? In procurement, the acronym RFX means Request for X, where X is a variable that stands in for different types of bid invitation...Spend Under Management: An Essential Guide
Taking Control of Your Spending In today's competitive business landscape, managing your expenses effectively is more important than ever. But with a... - Materials Management
Construction Materials Management: An Essential Guide
While most people identify construction material management with purchasing and distributing construction materials, the reality is more complicated.... - Supply Chain Management
One Size Compliments Most: Current SCM Provides Competitive Advantage to Engineering Firm
Melissa Stockley, a supply chain expert at Vista Projects, has fond memories of the 90s but doesn’t want to be “stuck there.” Stockley spent the... - Commentary
See You at CONEXPO-CON/AGG in Las Vegas?
A quick look at our date wheel reminds us that CONEXPO-CON/AGG is approaching fast! This will be our first time attending the largest construction show... - Expediting
Expediting in Procurement: An Essential Guide
Imagine a smoothly running assembly line, a construction project on schedule, or life-saving medical equipment delivered on time. These achievements all... - Current SCM
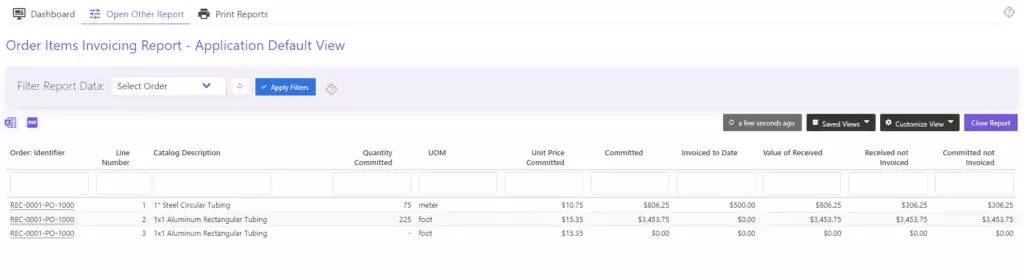
Line Level Invoicing and Invoice Attestation for Purchase Orders
We are excited to announce we have launched enhanced invoicing functionality within Current SCM! The system now supports tracking and cost allocations at...Offer Price Comparison & Historical Purchasing Data
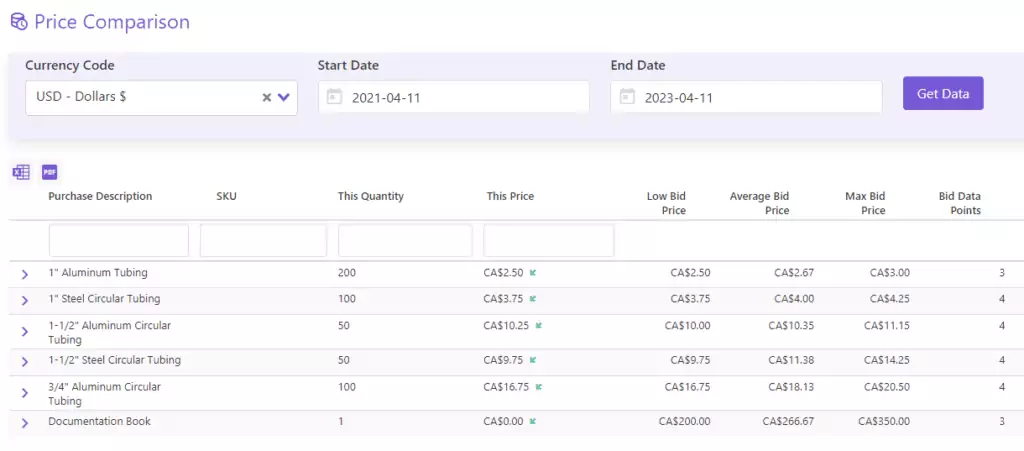
The Data You Need to Make Informed Procurement Decisions We are excited to announce we recently launched two new feature sets into Current SCM. Both...